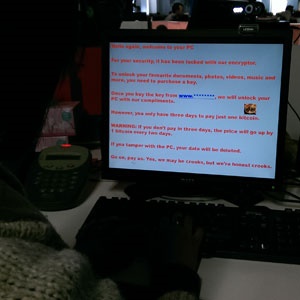
Cape Town – Ransomware has emerged as one of the more lucrative forms of cybercrime because of the low risk of being caught.
Cyber criminals deliver ransomware through malicious email attachments, social media and infected websites. They demand payment for unlocking personal files on PCs.
A number of South Africans have reported ransomware infections and some have been forced to pay thousands in an effort to get their data back.
“In one case a Panda client came back to us within 24 hours of installing Adaptive Defence after they were notified that Locky had been detected and blocked from accessing their network” said Jeremy Matthews, country manager for Panda Security.
READ: How ransomware has cost Fin24 users thousands
Locky, or Trojan-Ransom.Win32.Locky, is the most recent Trojan associated with ransomware scams and South Africa is the sixth most targeted country.
Top tips
“Ransomware generally works in one of several ways. Crypto ransomware can infect an operating system so that a device is unable to boot up. Other ransomware will encrypt a drive or a set of files or file names,” said Paul Williams, major account manager for Fortinet.
“Some malicious versions have a timer and begin deleting files until a ransom has been paid. All demand that a ransom be paid in order to unlock or release the blocked or encrypted system, files, or data,” he added.
Williams has 10 tips to protect yourself from the effects of ransomware:
1. Develop a backup and recovery plan. Back up your systems regularly, and store that backup offline on a separate device.
2. Use professional email and web security tools that analyse email attachments, websites, and files for malware, and can block potentially compromised advertisements and social media sites that have no business relevance. These tools should include sandbox functionality, so that new or unrecognized files can be executed and analysed in a safe environment.
READ: Here's how ransomware hits SA
3. Keep your operating systems, devices, and software patched and updated.
4. Make sure that your device and network antivirus, IPS, and antimalware tools are running the latest updates.
5. Where possible, use application white listing, which prevents unauthorized applications to be downloaded or run.
6. Segment your network into security zones, so that an infection in one area cannot easily spread to another.
7. Establish and enforce permission and privilege, so that the fewest number of users have the potential to infect business-critical applications, data, or services.
8. Establish and enforce a BYOD [Bring your own device] security policy which can inspect and block devices which do not meet your standards for security (no client or antimalware installed, antivirus files are out of date, operating systems need critical patches).
9. Deploy forensic analysis tools so that after an attack you can identify: a) Where the infection came from, b) How long it has been in your environment; c) That you have removed all of it from every device; d) That you can ensure it doesn’t come back.
10. For business, the weakest link in the protection chain is the end user, he added.
“Do not count on your employees to keep you safe. While it is still important to up-level your user awareness training so employees are taught to not download files, click on email attachments, or follow unsolicited web links in emails, human beings are the most vulnerable link in your security chain, and you need to plan around them,” said Williams.
He said that for many people, the internet is integral to their jobs and phishing attacks (targeted spam) have become convincing.
“A targeted phishing attack uses things like online data and social media profiles to customise an approach,” said Williams.
Experts advise people affected by ransomware not to pay, as there is no guarantee that cyber crooks will decrypt your data or demand further payments.
Watch this online video on how ransomware works:
- Follow Duncan on Twitter




 Publications
Publications
 Partners
Partners











